This post was authored by Fareed.
This blog post will discuss the security advisory, overview of the exploit, and technical analysis of the Follina MSDT attack that happens recently in the wild. This blog post might useful for security engineers, researchers, and security analysts to catch up with current cybersecurity issues specifically malware threats and APT hunting as the exploit has spread in the wild and been mentioned by a few security researchers on Twitter. By the end of this blog post, readers will understand the exploitation that happened to the compromised user via a malicious document using CVE-2022-30190 aka Follina attack technique. Furthermore, security analysts can collect the given IOCs extracted from the malware to check whether your environment has been compromised or not.
Introduction
On May 27, security researchers from the Nao_sec team posted a tweet regarding an interesting malicious document that loads a malicious external link (HTML file) residing in the remote server which then uses the "ms-msdt" scheme to execute PowerShell code upon the malicious document opened. This unique sample and technique caught all security practitioners and researchers including the NetbyteSec team. Figure 0 below shows Nao_sec's Twitter post.
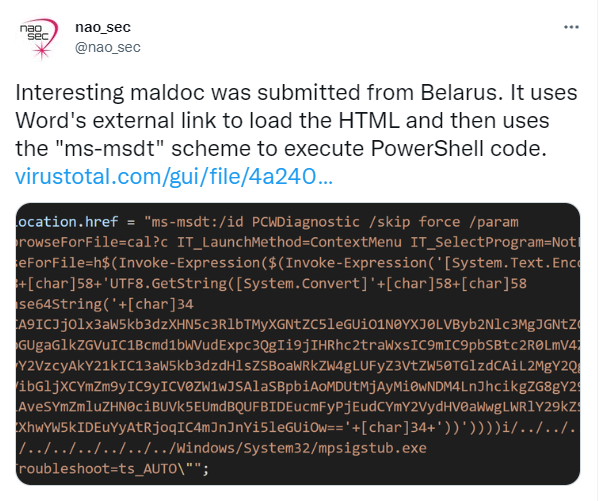 |
| Figure 0: Nao_sec's Twitter post |
On 30 May 2022, Microsoft released the CVE identifier for the vulnerability which is CVE-2022-30190 while infosec people on Twitter call this Zero-Day attack technique as Follina. Microsoft and infosec people have reported active exploitation of this vulnerability in the wild since April 2022.
 |
| Figure 1: Microsoft Support Diagnostic Tool interface |
Microsoft Support Diagnostic Tool (MSDT) is a diagnostic tool that collects information and sends it to Microsoft for analysis when users encounter certain issues. Microsoft uses this information to find solutions for the problems encountered by users. "A remote code execution vulnerability exists when MSDT in Windows is called using the URL protocol from a calling application such as Microsoft Office Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application." Microsoft said. The attacker can then take over the system, run malicious code and conduct post-exploitation activities without relying on Macros anymore.
Overview of the attack
%20(1).jpg) |
| Figure 2: Follina malicious document flow |
The malicious document could be delivered in DOCX, DOC, or RTF format. All the format works well to exploit this MSDT scheme vulnerability. The attacker craft the malicious HTML and serve the URL to the remote server to be loaded by document.xml.rels in the document. While RTF, the HTML URL is located under object control word and will be loaded upon opening the RTF or previewing the RTF via the preview pane. After HTML is loaded, it will trigger the ms-msdt scheme and continue to execute the malicious PowerShell code. The impact of the attack might result in the user being infected with the post-exploitation activities and malware infection.
Impact of the attack
Remote code execution and malware host/infection. An attacker who successfully exploits this vulnerability can run arbitrary code and take control of an affected system which can cause disruption in the organization's operation, data leakage, and many more.
Vulnerability Affected Products
- Windows Server, version 20H2 (Server Core Installation)
- Windows Server 2022 Azure Edition Core Hotpatch
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012 R2
- Windows Server 2012
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows RT 8.1
- Windows 8.1
- Windows 7
- Windows 11
- Windows 10
- Windows 10 Version 21H2
- Windows 10 Version 21H1
- Windows 10 Version 20H2
- Windows 10 Version 1809
- Windows 10 Version 1607
Proof-of-Concept
Researchers have reproduced the zero-day with multiple versions of Microsoft Office and even publish their Follina malicious document generator on GitHub. Netbytesec team also was able to conduct the Proof-of-Concept of the MSDT exploit which allows us to execute the calc.exe program as shown in the figure below.
 |
| Figure 3: MSDT exploit POC |
The attack is very simple to reproduce and all we need is to create a dummy document with an OLE object and save it. Then modify some important attributes in word/_rels/document.xml.rels and serve the HTML with the ms-msdt scheme at http://<attacker>/payload.html. Thus, this exploit technique might be popular from now on for malicious document weaponization purposes.
The figure below shows the payload.html being serve on the remote machine containing the MSDT scheme to execute our PowerShell code, in this case, "calc.exe".
 |
| Figure 4: HTML with the ms-msdt scheme |
Furthermore, the attack also appeared to be triggered by preview pane where all we need is to let the victims preview the malicious RTF file via the preview pane and they will get pwned without even opening the file. This attack vector might be overlooked by victims. So, the zero-click attack for the RTF in this situation is legitimate.
 |
| Figure 5: POC of the preview pane attack vector |
So, basically, the other attacker might replicate the zero-day attack by:
- Unzip the first discovered sample
- Replace the "Target" attribute of oleObject type with their remote HTML. Refer to figure 6 below.
- Zip the file and save it as DOC, DOCX, or RTF.
- Create and generate the HTML and serve it on the internet.
- The HTML must be at least 4096 bytes as mentioned by a security researcher on his Twitter.
- The code should contain in $() to PowerShell to execute it.
 |
| Figure 6: Change the original URL with the new URL |
Note that some attackers might encode their PS code with base64 like the sample discovered by the Nao_sec team. Figure 7 below shows the malicious encoded PowerShell code in the HTML file.
 |
| Figure 7: Encoded Powershell code in Nao_sec shared sample |
After the Nao_sec team's tweet post blew up, a few security researchers investigated and create their Proof-of-Concept and publish it on their GitHub as shown in figure 8-10 below. With all this shared POC, it will be easier for an attacker to replicate the attack.
 |
| Figure 8: POC by John Hammond |
 |
| Figure 9: Another POC and step by step instructions |
 |
| Figure 10: POC by chvancooten |
Process behavior: SysMon and ProcMon perspective
Observing the process behavior analysis based on SysMon and ProcMon monitoring results, we can see that the malicious document leverages the ms-msdt scheme to execute the attacker's malicious PowerShell code. Figure below shows the msdt.exe program run the ms-msdt scheme to execute the malicious code under the parent process Microsoft Word's application. So, a spawned msdt.exe process under the WINWORD.EXE process should be aware.
 |
| Figure 11: Winword.exe spawned msdt.exe containing the malicious msdt scheme |
As the Sysmon artifacts are also valuable to us, we can see that a Process Create action was detected in the Sysmon showing that a program msdt.exe were launched with the CommandLine containing the malicious msdt scheme executing PowerShell code (run our calc.exe program).
 |
| Figure 12: Sysmon showing the process creation of msdt.exe with the malicious commandline |
Moreover, the actual process that calls the calc.exe is sdiagnhost.exe via Conhost.exe as the child process as shown in the figure below.
 |
| Figure 13: The payload (calc.exe) will be spawned as a child process of sdiagnhost.exe |
Observing the Sysmon log below, our payload process (calc.exe) has been created with Parent Image
sdiagnhost.exe.
 |
| Figure 14: sdiagnhost.exe is the parent process of our calc.exe payload |
In such a way, keeping our eye on the child processes of msdt.exe and the sdiagnhost.exe would be enough to monitor this type of attack.
Technical Analysis
Netbytesec team retrieve some of the samples in the wild including the sample shared by the Nao_sec team on their Twitter and analyze how the exploit works and was able to reproduce the attack as mentioned in the proof-of-concept section.
Samples overview
Netbytesec team analyzed some samples in the wild including the one from the Nao_sec tweet which is 05-2022-0438.doc (MD5: 52945af1def85b171870b31fa4782e52) uploaded from Belarus. This sample does not conduct using any theme as the content of the document is a plain document.
Also, reports said some samples using this Follina attack have been
discovered targeting the Philippines.
 |
| Figure 15: CSAFP'S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx |
Back in April 2022, two samples were identified by security researchers uploaded to VirusTotal targeting Russia as the attacker using Russia-themed to lure victims. Figure 16 and 17 below show the Russia-themed document abusing MSDT.
 |
| Figure 16: приглашение на интервью.doc (invitation for an interview.doc) sample |
 |
| Figure 17: РЭТ-ЮМ-3044 от 12.04.2022.doc (RET-YUM-3044 from 04/12/2022.doc) sample |
Both of the above samples share the same remote server URL which is hxxps://www[.]sputnikradio[.]net
Another detected sample in the wild was submitted to VirusTotal in April of 2022. The document looks like luring victims using sexual issues.
 |
| Figure 18: Exposing_Sonish_Liar!!!.doc |
Another sample detected by Proofpoint spotted that China advance persistent threat group exploiting Follina as shown in the tweet below. With such a piece of news, organizations and the blue team should be more careful and keep an eye on this attack in their environment.
 |
| Figure 19: https://twitter.com/threatinsight/status/1531688214993555457 |
On 3rd June of 2022, another sample was raised exploiting Follina but this time, the attacker crafted the document and save it as an RTF file.
 |
| Figure 20: Malicious RTF content regarding employment agreement (242d2fa02535599dae793e731b6db5a2) |
05-2022-0438.doc analysis
MD5 hash: 52945af1def85b171870b31fa4782e52
The malicious document that uses this vulnerability contains the file "document.xml.rels" located in "\word\_rels" that loads the malicious HTML residing in the attacker's remote server at hxxps//www[.]xmlformats[.]com as shown in the figure below.
 |
| Figure 21: The document loads HTML upon opening the document |
Further investigation of HTML will show the PowerShell code used by the attacker in abusing the ms-msdt vulnerability.
 |
| Figure 22: Encoded base64 PowerShell |
Decoding the base64 will give the readable malicious PowerShell code which is likely the malicious code performs some malicious actions.
 |
| Figure 23: Decoded base64 PowerShell |
Based on the PowerShell code in the above figure, the code basically:
- Assign cmd's full path into variable $cmd
- Runs the cmd.exe with a hidden window using Start-Process cmdlet
- Then it kills the msdt.exe program if it's running on the infected machine
- The code use for loops to iterate on each files and folders in %temp% folder to find a RAR file named 05-2022-0438.rar
- It moves the RAR file from the %temp% folder to the public user folder and saves it as 1.rar
- The code then checks for the MSCF file by checking the file header (TVNDRgAAAA) encoded in base64 in the 1.rar and saving it as 1.t
- The code will decode the 1.t (base64 encoded) file using certutil.exe program and save it as 1.c
- The code will expand the compressed file (1.c) to the current folder and execute rgb.exe residing in the 1.c
The why question for why the RAR file is being dropped to the %temp% is unknown yet. Our team also cannot able to retrieve the RAR file. So, further analysis for the RAR file can't be done.
手发机房接单-渠道报价单-全网最低价.docx analysis
MD5: 14aff46aaffbad783974ba819dba6e41
The second sample that Netbytesec retrieved using hxxp://coolrat[.]xyz as the remote server to serve their malicious HTML named Loading.html.
 |
| Figure 24: The document loads HTML upon opening the document |
Analyzing the HTML file shows that the attacker replaces the AAAA padding with dummy words.
 |
| Figure 25: malicious HTML |
The attacker replicates the attack by encoding their malicious PowerShell code with base64. Figure below shows the decoded version of the PowerShell.
 |
| Figure 26: Decoded PS code |
This time, the malicious code will download an executable residing in the C2 server and save it as temp.exe. The PowerShell code then executes the temp.exe using start-process.
Employment Agreement.RTF analysis
MD5: 242d2fa02535599dae793e731b6db5a2
The below picture shows the RTF contains an object referring to the malicious HTML remotely hosted at hxxp://45[.]76[.]53.253/1.html.
 |
| Figure 27: HTML payload in the object control word |
The third sample uses the classic AAAA padding in the HTML file like the famous one from Nao_sec and the payload msdt scheme's structure looks the same. The final payload of this sample will steal the user's system information and login data. The figure below shows the malicious HTML file used for the Follina exploitation.
 |
| Figure 28: HTML payload |
The attacker crafting the PowerShell payload with the base64 encoding which likely needs to decode to understand the malicious code. Base64 decoded version of the payload as shown below:
 |
| Figure 29: decoded payload |
The malicious PowerShell code firstly will get a process name msdt that is running on the local computer using the Get-Process cmdlet and terminate the process using the Stop-Process cmdlet. Next, the malicious code download and execute another PowerShell payload from their C2 server seller-notification[.]live which is what we call fileless execution. The malicious PowerShell code will run in memory without touching the disk.
Retrieve the PowerShell script in the URL revealing the payload will try to collect the infected machine's information, compress it into a ZIP file and upload the ZIP to their another C2 server at 45[.]77.156[.]179 on port 443. Figure 30 - 31 shows the content of the Zgfbe234dg code.
 |
| Figure 30: Lines 1 - 40 |
 |
| Figure 31: lines 41 -76 |
The code collect login data and information from browsers such as Firefox, email applications such as Outlook, SSH client applications, FTP clients, and remote desktop applications. It appears also that malware collect system information by running commands such as system info, ipconfig, and many more. In the last part of the code, the malware will compress all the collected files and data and save them as a ZIP file. The ZIP file will be uploaded to the attacker's remote server served at 45[.]77.156[.]179 on port 443.
Other samples analysis
All the remote servers for the available samples seem down when uploaded to the Virus Total. Thus, the Netbytesec team not able to do further analysis of the HTML.
The list below shows the malicious remote HTML serves by each of the other samples.
- CSAFP'S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx = hxxp://141[.]98[.]215[.]99/color.html
- приглашение на интервью.doc = hxxps://www[.]sputnikradio[.]net/radio/news/3134.html
- РЭТ-ЮМ-3044 от 12.04.2022.doc = hxxps://www[.]sputnikradio[.]net/radio/news/1134.html
- Exposing_Sonish_Liar!!!.doc = hxxps://exchange[.]oufca[.]com.au/owa/auth/15.1.2375/themes/p3azx.html
Detection
In terms of detection perspective, the malicious code is loaded from the remote component in the attacker's server, thus the document does not embed any malicious code in the files which will make detection a little bit harder as the malicious code is in the HTML file remotely serve on the internet instead of in the document like the Macro attack.
The YARA rule below can be use to detects the malicious document.
rule Follina_msdt_maldoc_DOC_XML_Rels {
meta:
description = "Detects for DOC and DOCX's Follina sample based on document.xml.rels file. You need to unzip the DOC/DOCX file and go to word/_rels/document.xml.rels"
strings:
$s0 = { 3C 3F 78 6D 6C } //<?xml
$s1 = "<Relationships" ascii
$s2 = ".html!" ascii
$s3 = "TargetMode=\"External\"" ascii
$s4 = "TargetMode = \"External\"" ascii
condition:
$s0 and $s1 and $s2 and ($s3 or $s4)
}
rule Follina_msdt_maldoc_RTF {
meta:
description = "Detects for RTF's Follina sample"
strings:
$s1 = "objclass http" ascii
$s2 = ".html}" ascii
condition:
uint32be(0) == 0x7B5C7274 and
all of them
}
rule Follina_msdt_HTML {
meta:
description = "Detects for malicious HTML uses to execute ms-msdt in Follina sample"
strings:
$s0 = { 3C 21 64 6F 63 74 79 70 65 } //<!doctype
$s1 = "window.location.href = \"ms-msdt:" ascii
condition:
all of them
}
If you're using SIGMA you might take a look at this rule here and here.
The Elastic team also has created and modified existing rules in order to detect MSDT attacks in Elastic which can be referred to here and here.
DFIR Artifact
Based on Nasreddine's tweet, the post-exploit forensics can be done to check whether a user got compromised or not due to the attack is by checking the log "PCW.debugreport.xml" located at %localappdata%\Diagnostics.
 |
Figure 32: PCW.debugreport.xml contains Follina log
|
The figure above shows that the executed PowerShell payload which is "IEX(calc.exe)" is being recorded in PCW.debugreport.xml which will be useful for Incident Response and Forensics activities.
Recommendations
No patch is available yet from Microsoft but users and administrators are recommended to review the Microsoft
guidance by
disabling Microsoft Support Diagnostic Tool (MSDT) URL Protocol and
perform the necessary steps to harden your Windows machines from the attack.
The figure below shows the ms-msdt registry key that needs to be deleted:
 |
| Figure 33: ms-msdt registry key |
Disabling MSDT:
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt any_filename“
- Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
 |
| Figure 34: Backup and delete ms-msdt key |
Microsoft also advises that "customers with Microsoft Defender Antivirus should turn on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats."
Also, people are advised to disable the preview pane in Windows Explorer to avoid such an attack regarding the preview pane attack vector.
Companies and organizations should be aware of users and their employees to be careful and stay alert when opening or receiving a document from an untrusted source. Identifying, detecting, and deleting malicious emails or attachments is the best thing we can do to defend against this threat until Microsoft release the official patch for this vulnerability.
Netbytesec team also recommended user use Anti-Virus or any security solution to minimize and detects this type of attack in their environment.
Conclusion
Netbytesec team concludes that the vulnerability or Follina attack is critical as the exploit is able to execute arbitrary code specifically malicious code in the perspective of security concern. The attack abuses the ms-msdt scheme to make the exploit work by delivering the attack vector via Microsoft Office documents format including DOC, DOCX, and RTF. Upon opening the malicious document, victims will completely be infected by the malicious code as the PowerShell code will be run in the background without the user's concern. The Follina has a zero-click attack if the attacker saves the document as RTF. The zero-click attack is triggered when victims enable the preview pane in their Windows machine and preview the malicious RTF via the preview pane. The attack is easy to replicate and reproduce. Thus, this type of attack will be seen a lot in the wild after this.
Indicator of Compromie (IOCs)
Samples' MD5 hashes
| Filename |
MD5 hash |
| CSAFP'S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx |
8ee8fe6f0226e346e224cd72c728157c |
| РЭТ-ЮМ-3044 от 12.04.2022.doc |
6bcee92ab337c9130f27143cc7be5a55 |
| приглашение на интервью.doc |
f531a7c270d43656e34d578c8e71bc39 |
| 05-2022-0438.doc |
52945af1def85b171870b31fa4782e52 |
| 手发机房接单-渠道报价单-全网最低价.docx |
14aff46aaffbad783974ba819dba6e41 |
| Exposing_Sonish_Liar!!!.doc |
529c8f3d6d02ba996357aba535f688fc |
| Employment Agreement |
242d2fa02535599dae793e731b6db5a2 |
Command and Control Server
- 141[.]98[.]215[.]99
- www[.]sputnikradio[.]net
- www[.]xmlformats[.]com
- coolrat[.]xyz
- tibet-gov[.]web[.]app
- exchange[.]oufca[.]com.[]au
- 45[.]76[.]53.253
- 45[.]77.156[.]179
- seller-notification[.]live
Reference and further reading
- https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
- https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug
- https://gist.github.com/tothi/66290a42896a97920055e50128c9f040


%20(1).jpg)































